I finally bothered to create an automated backup workflow for my critical data.7 min read
I’ve played fast and loose with my data for a while now, never really concerned with the possibility of losing something. My data was...

Automating Weight Loss Tracking with Lose It!, OneDrive, Power Automate, and Splunk5 min read
About 2 months ago, I decided I was tired of how much I weighed and would do something about it. I went to see...
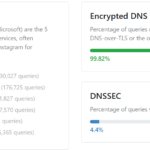
Updating my home network with scalable, configurable, and multi-group DNS4 min read
It’s been a while since I last made any significant updates to my home network; almost 2 years, in fact. The network has gone...

You need to block .zip and .mov URLs RIGHT NOW!2 min read
This is not a drill; repeat, this is not a drill! Google recently announced 8 new Top Level Domains (TLDs) that users can purchase...
Lesson 6: Blackhat is Mostly Pointless: My Thoughts on Casper Malware5 min read
Earlier today, my boss sent me this news article with two questions: Now, I’ve firmly believed in reading the news for your boss so...
Adding Redundancy Into My Network and the Value of Planning3 min read
In this post, I wanted to say some of the lessons I’ve learned with maintaining a relatively large home network and a bit of...
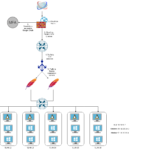
A Major Update to My Training Lab14 min read
I first documented my training lab a few years ago and then discussed it again when talking about how I set up Proxmox with...
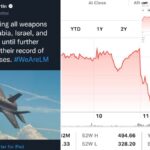
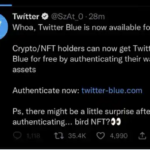
Twitter, Lockheed, and the CIA triad3 min read
A "verified" account crashed the stock of a multibillion-dollar company....
Vindication: The Value of Listening to Your Gut5 min read
I don’t usually make posts that could be in the vein of “I told you so,” but my last post received such unfounded vitriolic...
