I don’t usually make posts that could be in the vein of “I told you so,” but my last post received such unfounded vitriolic backlash that I feel compelled to defend myself. In my previous post, I made a cardinal sin; I mentioned Elon Musk on Reddit.
For some background context, I usually post one of two things on my blog; technical posts and thought pieces. Most posts are technical walkthroughs of something I had recently done, but occasionally I’ll post a thought piece where I share my opinions on the industry. My last post on blocking t.co was firmly in the latter category. I usually post my thought pieces to Reddit’s cybersecurity Sub-Reddit without any links to my blog. I do this because I want to get the communities opinions on my thoughts without spamming my blog, and usually, the community has been very receptive to ideas. I’ve had good discussions on the various topics I’ve discussed. That was not the case with my post about t.co.
Within moments of posting on Reddit, I got accused of “letting my biases show” and “not removing my personal opinions about Elon and looking at the situation factually.” Someone even claimed I was “…upset because ‘bad man’ bought Twitter. [sic]” Almost no comment addressed any point I brought up about phishing campaigns leveraging the inherent trust we place on an external service varifying users. One reply did argue that we should go to explicit whitelisting for the internet (something that has never been successful and will probably never be successful). My response to this was challenged in that I needed to provide intricate detail on how an NGFW filter works from the logical and hardware level and provide my certifications before I was allowed to explain why whitelisting doesn’t work on the internet. Most of the replies that weren’t outright accusing me of “pushing an Anti-Musk narrative” (an actual response I got) seemed to focus on the users sharing passwords through DMs, even though the post was clearly about phishing links. I was surprised by the backlash I received on this post.
I shouldn’t have been surprised, I have been using the internet since its inception decades ago, and vocal jerks are, unfortunately, far from uncommon. They’ve always existed in the earliest IRC chatrooms and most nascent forums. What I realized early in those days was something that I should have taken to heart two days ago when I wrote the post. I needed to write not to be understood but so that no one could misunderstand. I didn’t understand my audience when I wrote that post, and I didn’t consider the inherent biases that my readers would bring to the post. By starting the blog post with a discussion about Elon Musk buying Twitter, I inadvertently created a situation where the readers would assume that I was bashing Musk. To be direct, I have no opinions about Musk, good or bad.
The meat and potatoes
The real reason I wanted to write this post was not to whine about people on the internet being mean to me. I’m a grown adult; I can handle that. Instead, it was because the exact thing I predicted is happening two days after I expected it.
According to Digital Trends, users are abusing Twitter’s new verification process to masquerade as popular Video Game companies like Nintendo and Valve to engage in a bit of light trolling. These users created new accounts, copied the name and logo of the legitimate Nintendo account, and then “verified” themselves using the Twitter Blue process. Following this, they sought to sow chaos by announcing things that don’t exist, making public statements on behalf of the country, and posting vulgar photos of beloved characters.
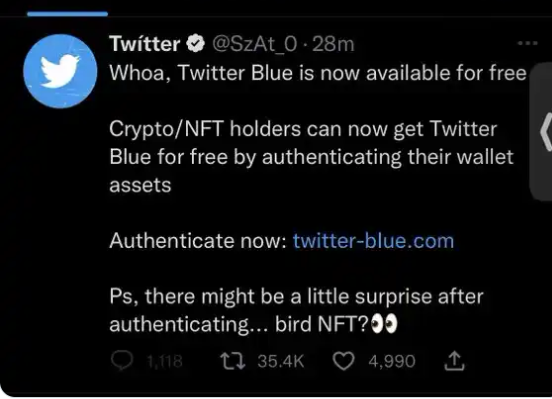
While this is thankfully only trolling at its finest, it eludes to a darker underbelly. For every Nintendo imitator, how many are imitating celebrities for phishing? Less than 24 hours after my blog post, I saw this tweet from someone pretending to be Twitter and directing people to a crypto mining website. This Tweet was retweeted almost 36K times. As mentioned in my original post, all links on Twitter use a shortcut of t.co, even if they display the regular domain. Blocking t.co will stop any user from going to any phishing domain by clicking on the link.
I was informed in my original post that Twitter will implement a verification-checking process where users must provide authentication to verify themselves and that changing your name on Twitter will result in the loss of verified status until you re-authenticate. That sounds like an excellent step, although I’m hesitant to believe users will ever accept it. Facebook attempted a similar process years ago where every account was supposed to be a “true user.” Users would need to prove they are a real person, and their account must match their actual identification. The community thoroughly rejected this, and Facebook never implemented it. I expect the same will happen with Twitter.
Additionally, the way things will be and how things are currently differ dramatically, and we must defend both. We cannot afford to ignore immediate threats to our networks because someone else might implement a process that nullifies the danger in the future. We need to block immediate threats immediately and reevaluate when conditions change. And make no mistake, this is a legitimate threat now. This will be a threat until Twitter gets a handle on the verification process.
I firmly stand behind my original post that Twitter Blue’s new process will increase phishing attacks and that we, as defenders, need to curb that until Twitter implements authentication. I predicted it, and despite the backlash I received from people who didn’t bother reading, I trusted my gut feeling. Trust your gut, and don’t let the vitriolic backlash make you doubt yourself. You should not be ashamed if your analysis and reasoning are solid, but keep your audience in mind when you write.