It’s been a while since I last made any significant updates to my home network; almost 2 years, in fact. The network has gone through some essential updates, but nothing that would generate a new Network map overall.
The 2021 major update has served my family’s needs for a long time but did have some inconveniences that I was willing to ignore for simplicity. When I set up the network and deployed services to handle things like security and adblocking, I did so with an overarching baseline in mind. The security blockers would block everything from adult content to privacy trackers to anonymizers. This caused a few issues for my wife and I.
More specifically, blocking ads across the entire home caused my wife issues. Adblockers will frequently block the top links in Google search results. Google will sell space above the actual search results as ads. These ads are what my wife likes to click on. Additionally, she wants to use services like Rakuten to earn rebates from online shopping; adblockers also block these.
Blocking these “features” caused significant irritation to my wife (the user), resulting in her not using the Wi-Fi on her phone most of the time. By removing herself from the Wi-Fi, she also removed herself from the protections provided by the DNS blackhole. She no longer benefited from things like phishing protection, malware protection, and tracker protection. This concept of cyber empathy and what it means for security are a topic I’ll address in a different blog post.
I needed a new way to handle my DNS blackhole and the benefits it provides. I’ve previously talked about pfBlocker-ng and discussed how I use it. I’ve also compared pgBlocker to adguard and Pi-hole, where I ranked Adguard Home as the best of the three but liked that pfBlocker was built into the router. Unfortunately, as I worked through how I wanted to make this, I ran into a significant issue with pfBlocker; there’s no group management.
Unlike in Pi-Hole or Adguad Home pfBlocker has no way to specify which ad lists apply to which hosts. You can determine that no ad lists apply to individual hosts, but you can’t select some lists. It’s either all or no lists, leading to the abovementioned issue.
So, I began to redesign. As always, I had some requirements;
- My wife would need to be able to click on affiant links while still being protected from malware and phishing links.
- Additionally, I’d like to block ads for her.
- I need the ability to conduct my security research in my malware Lab. (i.e., the security settings should not affect my research devices)
- My Kids need internet access but with heavy restrictions on adult content, social media, and search filters.
Additionally, I had some bonus objectives I wanted to establish;
- I wanted to maintain logs for months.
- I wanted my DNS requests encrypted with DoT and obfuscated from my IP.
With my requirements established, I got to work.
The above graphic is a very loose version of my network setup. I set up a new VLAN to handle my management systems. I should have done this a year ago but never got around to it. After setting up this management VLAN, I set up two Adguard Home servers on small Ubuntu LXC containers.
Next, I modified all my firewall logs to send DNS traffic to those LXC containers and set the DHCP server to issue the LXCs as the DNS IP.
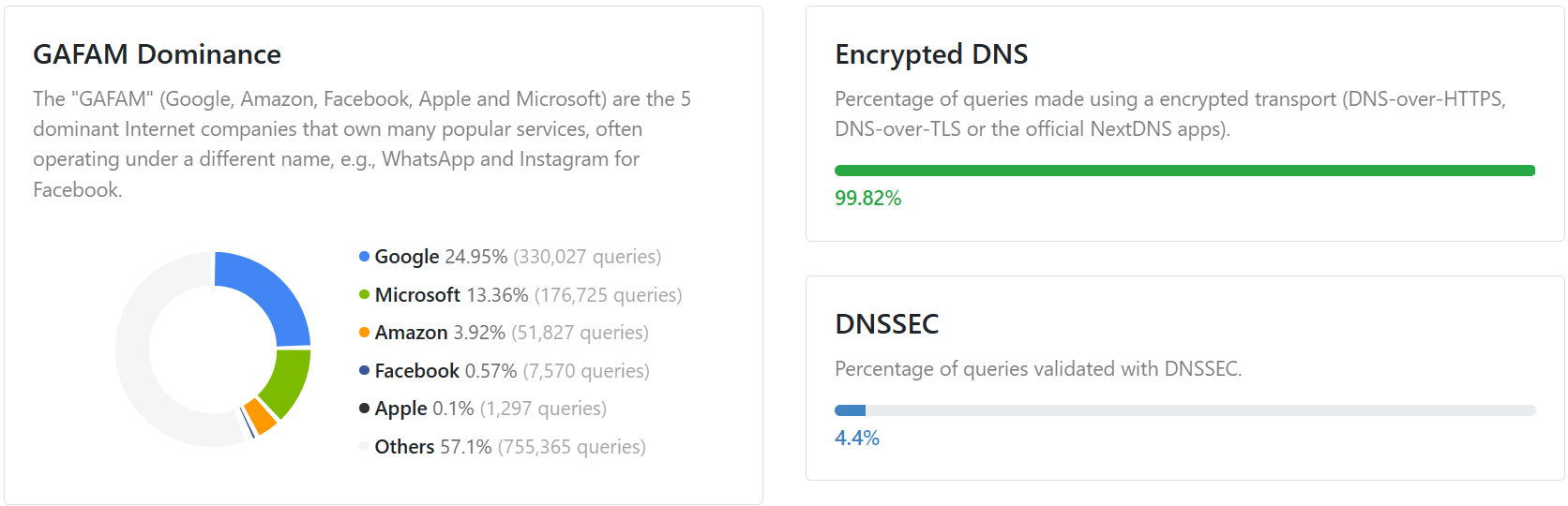
To handle the upstream resolving, I purchased a yearly subscription to NextDNS (a topic I’ve recommended in my advice to parents). NextDNS allows you to set different DNS groups with other associated policies. One important thing about the NextDNS groups is that each group has a unique DoT address.
Finally, after establishing the NextDNS groups, I returned to Adguard Home. I made custom groups for each important device (My personal devices, my wife’s personal devices, and my kids’ personal devices). After that, I marked each one with their designated NextDNS DoT address.
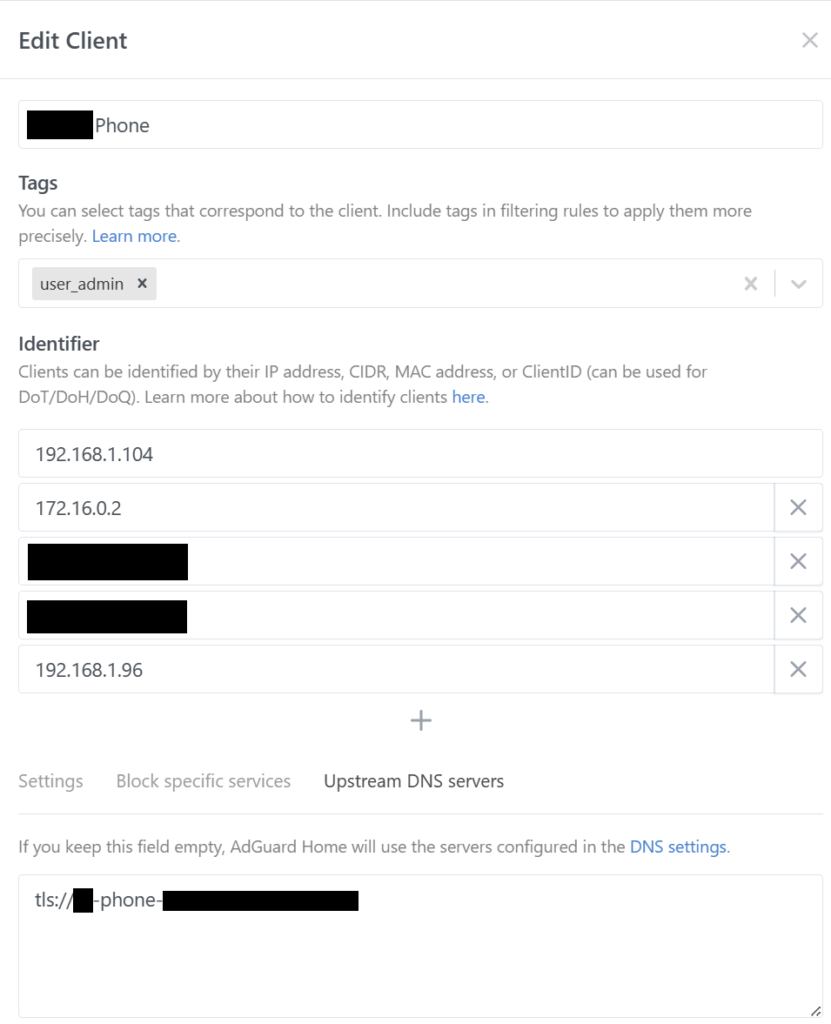
I then set a “catch all” network to handle requests from anything not deemed critical enough to track its requests directly, while guest users had their own heavily locked down group.
Finally, I had all the Management VLAN go over my privacy VPN.
Conclusion
The result was that each person in my house had custom blocklists tailored for them. My wife can click on ads while protected from malware and phishing, I can conduct research while blocking ads and trackers, and my kids can do school work while not being able to access Social Media and have safe search enforced (plus adblocking). My Adguard Home server stores 90 days of logs, with the NextDNS server holding 2 years of records associated with a privacy VPN IP.

