Category: Uncategorized
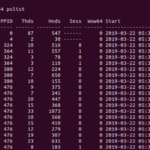
Solving the DEFCON 2019 Volatility Memory Forensics CTF16 min read
A few months ago I found the DEFCON2019 Volatility Memory Forensics challenge and decided to take a look. Memory Forensics are a personal favorite...
Cybersecurity Project: How I broke into the field16 min read
A quick forward with some background on this before I begin; a few days ago, one of the mods of the r/cybersecurity subreddit (which I highly...
Setting up the Training Lab for Remote Learning9 min read
Several years ago I started volunteering to help teach people an introduction to Cybersecurity. At the time it was easy to work with my...
Keeping your kids safe online23 min read
Online Safety and Kids The internet can be a scary and dangerous place, especially for kids. Our world continues to move more and more...
Can we stop saying Google sells your data now?5 min read
In the online world of data scandals and the fight for online privacy, Google has had a rough few years. Seemingly overnight the behemoth...
Is “Safe Browsing” all I need to do to stop malware?6 min read
BLUF BLUF: No safe browsing practices are a good start but even trustworthy websites can have malware. Chances are someone at some point has...
What is Double NAT and how does it affect me3 min read
If you spend anytime reading technical forums you’ve likely heard the phrase “Double NAT”. People like to talk about Double NAT like it’s the...
Is Apple really as privacy focused as they market?6 min read
The short answer: No. Apple sells advertising space the same as Google does. Most of us have probably seen this ad before: It’s simple...
Do you really need a VPN?6 min read
If you’ve spent any time on YouTube recently then chances are you’re heard a Youtuber promoting Nord VPN. Before I begin with this, I...
Vulnerability vs. Exploit vs. Payload vs. Zeroday4 min read
The longer I’m in the world of Cyber Security the more I realize that people like to throw these phrases around seemingly interchangeably. The...
