Do you really need a VPN?6 min read
If you’ve spent any time on YouTube recently then chances are you’re heard a Youtuber promoting Nord VPN. Before I begin with this, I...
Vulnerability vs. Exploit vs. Payload vs. Zeroday4 min read
The longer I’m in the world of Cyber Security the more I realize that people like to throw these phrases around seemingly interchangeably. The...
It’s time to stop blaming the End User and adopt a new security strategy4 min read
If you’ve ever worked in IT before you’ve heard the phrase “PEBKAC”; problem exists between keyboard and chair. We use this phrase to say...
Google Wi-Fi Review: Simple Mesh for Simple Needs7 min read
Several years ago, I bought a Google Wi-Fi Mesh system to solve a problem my wife was having. I fell in love with the...

An Update to the VLAN Situation10 min read
Intro A few days ago I wrote an article about adding VLANs to my home network in order to segment off my IoT devices....
Why you should be using MAC filtering on your Wi-Fi, and other things5 min read
Intro MAC address filter has been an option on almost every router for a decade or longer. The concept is simple; every device has...
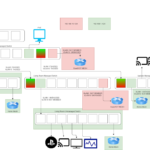
Adding VLANs to my home network7 min read
Background A little over a year ago I wrote a blog post taking a retrospective look at my home network. It was pretty fun...
What can someone do with your IP address14 min read
The real truth from someone who isn’t trying to sell you a VPN: Also a reason why you should avoid Nord. For those of you...
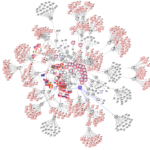
Threat Hunting with OSINT: Uncovering a Crypto-Mining Botnet21 min read
Preamble: Safety first Before I begin with walking through this I want to remind everyone to remember safety first. I am working with live...
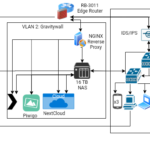
A Retrospective Look at my Home Network Progression14 min read
Introduction If you’ve spent any time in the world of cyber security, you’ll know that one of the things expected is continuous learning. As...
