Ads suck. That’s why I don’t run any.
Ads have dominated the internet over the last decade, it’s hard to go to any webpage now without being bombarded by ads taking over most of your screen. On computers we have the ability to install adblockers like the fantastic uBlock origin but outside of work most people aren’t using a standalone computer anymore.
Here’s some anecdotal evidence; I work in tech, big surprise I know. We have new adults join us all the time either fresh out of high school or fresh out of college. When people join us we put them through a training program that involves downloading and setting up a Linux virtual machine. In recent years this training has become increasingly difficult to do as a substantial portion of our new hires aren’t able to set up a virtual machine because they only have an iPad or they use their phone for everything.
While that was somewhat tangential it does Segway nicely into my next point. Adblocking extension on a PC works fine, but if you don’t have a PC then what can you do? This is where DNS based adblocking comes into play.
Adblocking DNS is technically a new(ish) usage of an old(ish) technology. Specifically what I mean by that is that DNS based website blocking has existed for years as a security tool. Transparent SSL/TLS Man in the Middling to decrypt and block websites became an extremely difficult and costly endeavor. However, there was still a need to block websites; enter DNS sinkholing. DNS sinkholing works by maintaining a list of domain names you want blocked, then when the DNS server receives a request for those domain names it resolves the domain to something non existent like 0.0.0.0 or to it’s block page rather than to the legitimate IP.
DNS sinkholing used to be a corporate specific thing but now its not only common place but extremely easy to set up thanks to the excellent work of the folks behind the Pi-Hole project which, as far as I can tell, were the catalyst behind most or all of the projects I’m going to mention today.
We can use DNS sinkholing today to block ads across a network by blocking the domains which server ads. Today I’m going to talk about 3 different free and open source DNS based adblockers for your home.
Pi-Hole
Pi-Hole was one of the first free and open source DNS based adblockers and one of the first projects I set up in my home network. The team behind Pi-Hole have done an amazing job creating such a useful product, it was one of the products I recommend to parents looking to implement some content filters to protect their kids. I ultimately stopped using Pi-Hole and replaced it with pfBlockerNG but that was less due to anything Pi-Hole related and more to due with my attempts at consolidation. Never-the-less lets take a look at how Pi-Hole is today.
Set up
Pi-Hole is still a super easy install thanks to the one line installer found on https://pi-hole.net. From there the Pi-Hole has a few yes or no questions and you’re off to the races. When I set up Pi-Hole years ago it used to ask you what static IP you wanted and what the subnet was. This could become complicated for people who aren’t very familiar with how networking works. Thankfully that portion is removed and now you get a notification telling you that you need to assign a static IP or you could run into problems.
The Dashboard
The dashboard looks dated by today’s standards. This is the same dashboard that has been used for the last 7 years. It looks alright and it does it’s job fine but it’s very 2015.
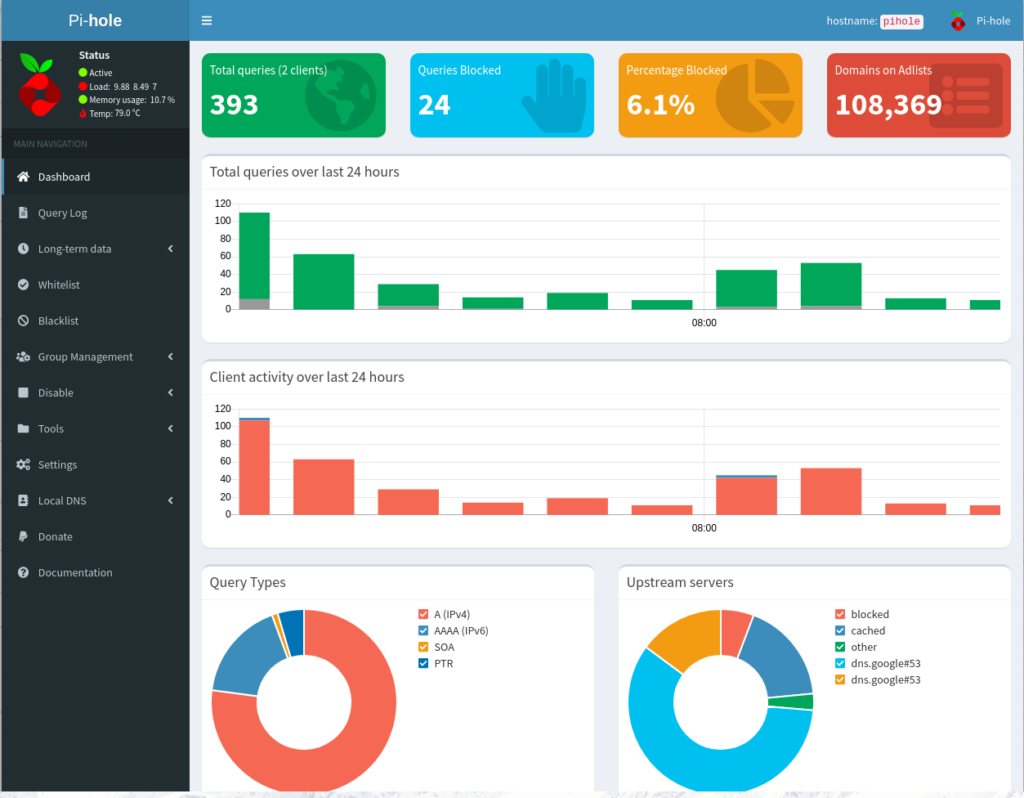
Part of my issue with this dashboard is that it’s complicated. Where do I manage add lists? They’re under Group Management. How do I remove a domain from showing up on the dashboard? Tools -> Audit Log -> Audit.
Features
Pi-Hole has a number of features which I really like; namely it’s group management. With Group management you can add specific clients to a group and then assign specific blocklists to those groups. Here’s an example where this becomes useful. I may want to block my kids from seeing violence so I add a violence related domain blocklist; however, I work for the military so some of the websites I go to include things MilitaryTimes. The blocklist might prevent me from reading the news about how the new Physical Training tests are going to be administered.
This is where Pi-Hole has a huge advantage. I can add my computers to an adult group and allow the adult group to go to websites that may contain violence (like Militarytimes). This is a fantastic feature and one that I miss in pfBlockerNG. Unfortunately however, that’s where the benefits of Pi-Hole end.
Another nice feature with Pi-Hole is the long term query storage. When it works it works well and you can go back quite a ways to do trend analysis or map out an intrusion.
Problems with Pi-Hole
While I love Pi-Hole, I ran one in my house for almost 6 years straight, it does have some issues. I’ve already talked about one of these problems before; the lack of SSL/TLS support.
Lack of SSL/TLS support
The Pi-Hole dev team refuses to implement an easy way to add HTTPS support to the web browser. The devs have stated that HTTPS support is not coming because people don’t need it. This completely flys in the face of good security. Not only will you have these devices publicly exposed on the internet, but attackers can and do sniff internal network traffic when they break into a network. Without SSL/TLS there to encrypt the traffic you’re exposing the credentials which allow access to the admin page. From there a malicious actor could overwrite the hosts file to have any (or all) dns requests redirect to an attacker page which downloads malware. Or at a more basic level they could simply shut down the dns server and thus DoS the network. There’s really no reason why Pi-Hole cannot have SSL/TLS support beyond the devs just not wanting to put it in.
Lack of Proper ACLs
Another issue I have with Pi-Hole is a lack of proper ACLs on it. Within Pi-Hole itself there is no way to limit which clients are allowed to query it. Now I know some of you are reading this and saying well that’s the role of the firewall to handle that, and you’re mostly correct. The firewall is one line of defense, but its not the only line of defense. Proper security engineering would have you apply defenses at every level including at both the firewall and application level. You should have a host level firewall that is filtering IPs and Ports but at the application level you can filter based off ClientID where you couldn’t in something like IPTables
Lack of “officially” supported encryption
In recent years and the wake of massive scandals like Cambridge Analytica people have become more increasingly aware of their privacy, and with it, more aware of how DNS logs can be used to get a profile of what a user does. To counter this data collection by ISPs technologies like DNS over HTTPs (DoH) and DNS over TLS (DoT) were created. With these technologies DNS queries are encrypted until they reach the upstream resolver which decrypts them. This means your ISP only sees an encrypted blob of text instead of a record that you went to blog.gravitywall.net.
Unfortunately, and despite an obvious interest from the community, Pi-Hole does not natively support DoH or DoT. There are plenty of guides online on how to set it up but it’s not built into Pi-Hole itself. In order to set it up you have to use the command line and configure it manually.
AdGuard Home DNS
AdGuard Home came out a few years after I got heavily invested in Pi-Hole or I might have considered it more. Now that I’m experimenting with it I’m actually discovering there’s a lot to like here and most of my complains with Pi-Hole are dealt with. AdGuard has a much larger name behind it than Pi-Hole does as well but that doesn’t matter that much. The AdGuard lists can also be imported into Pi-Hole, where AdGuard has an advantage is in features.
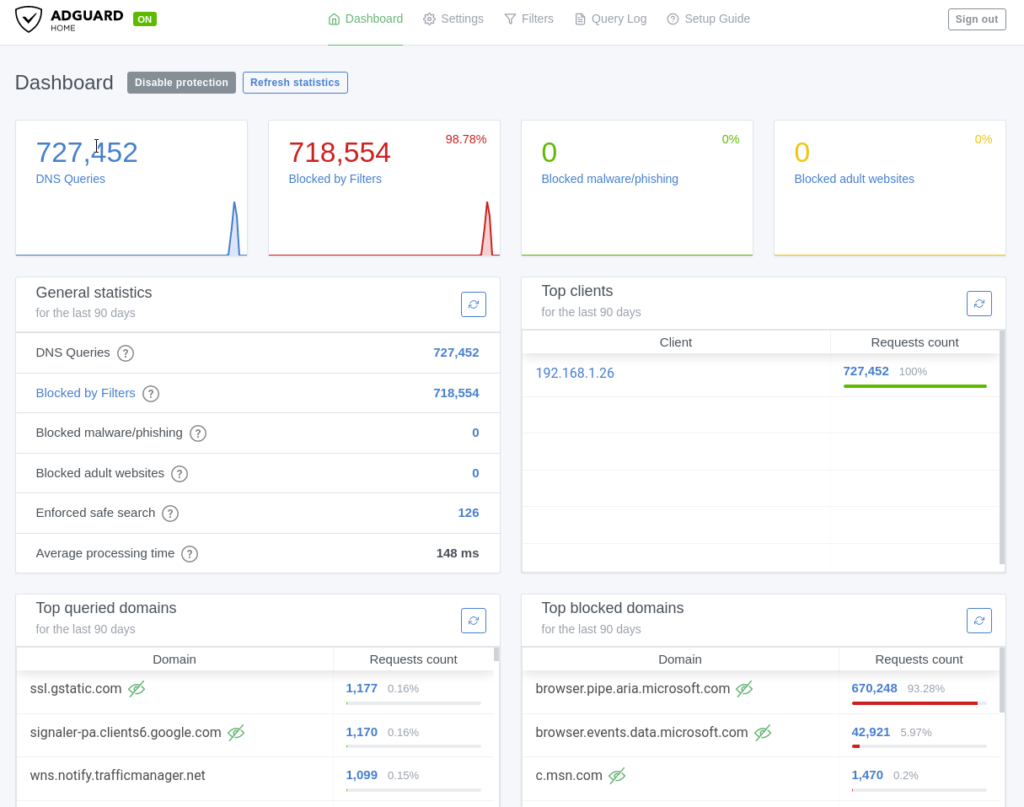
The Dashboard
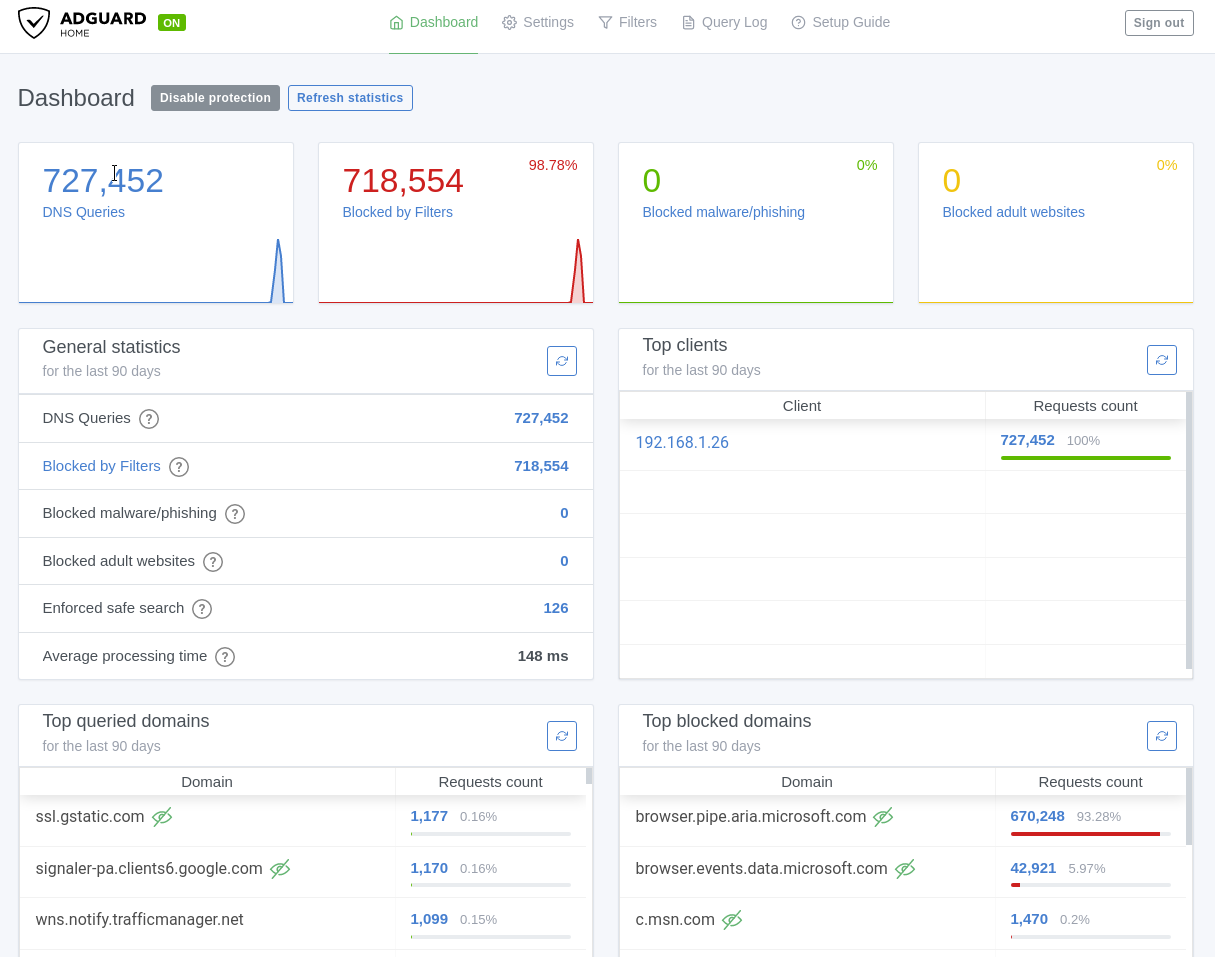
The AdGuard Dashboard looks much much better than the Pi-Hole dashboard. It embraces the minimalism aesthetic which has become common in tech recently. The at a glance widgets convey the things I care about most; my total queries, blocked amount (with %), how many malware queries were blocked, and how many adult websites were blocked. The page is hyperlinked to other parts of the application so I can go straight from the front page to seeing all my blocked queries, and only the blocked ones, with only one button click.
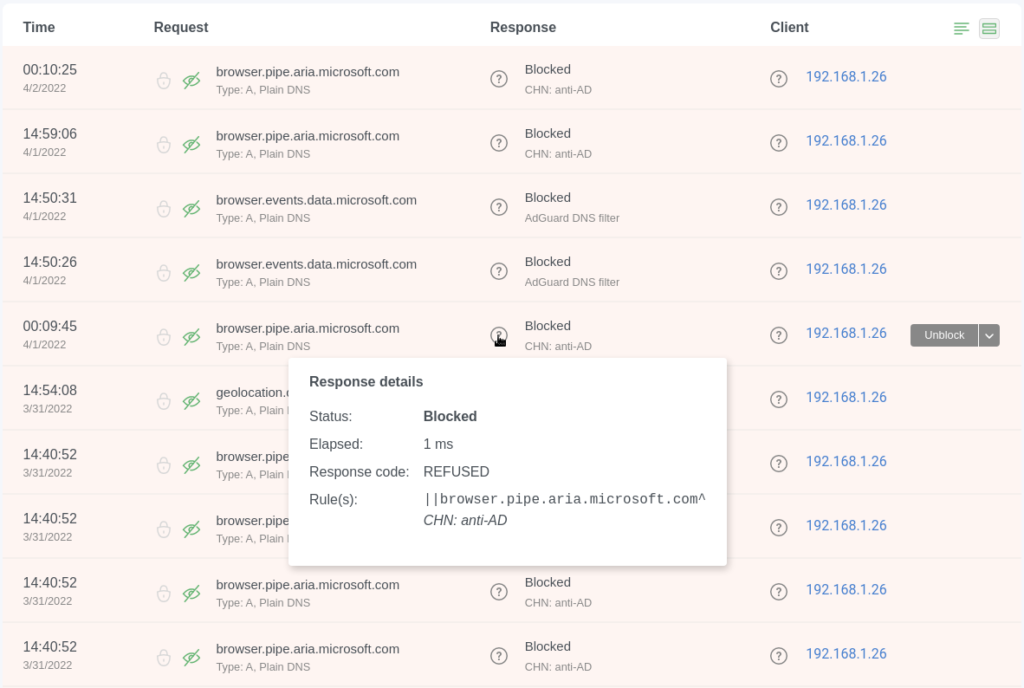
From the block page I can unblock domains entirely or for a single client directly as well as see exactly what rule in which list blocked that domain.
The dashboard also allows 1 click adding of blocklists rather than copy and pasting urls in (although that’s still an option)
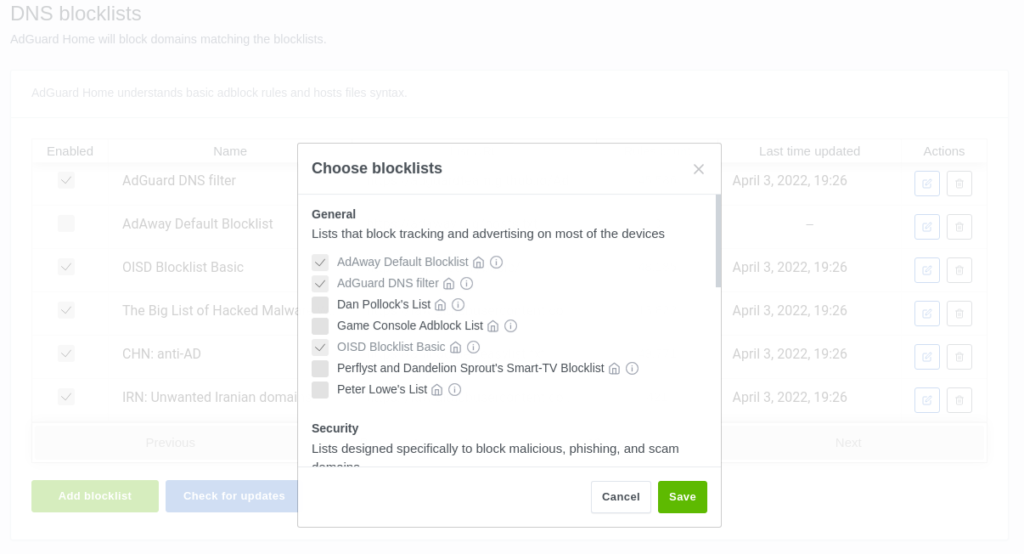
And easy filtering of specific services
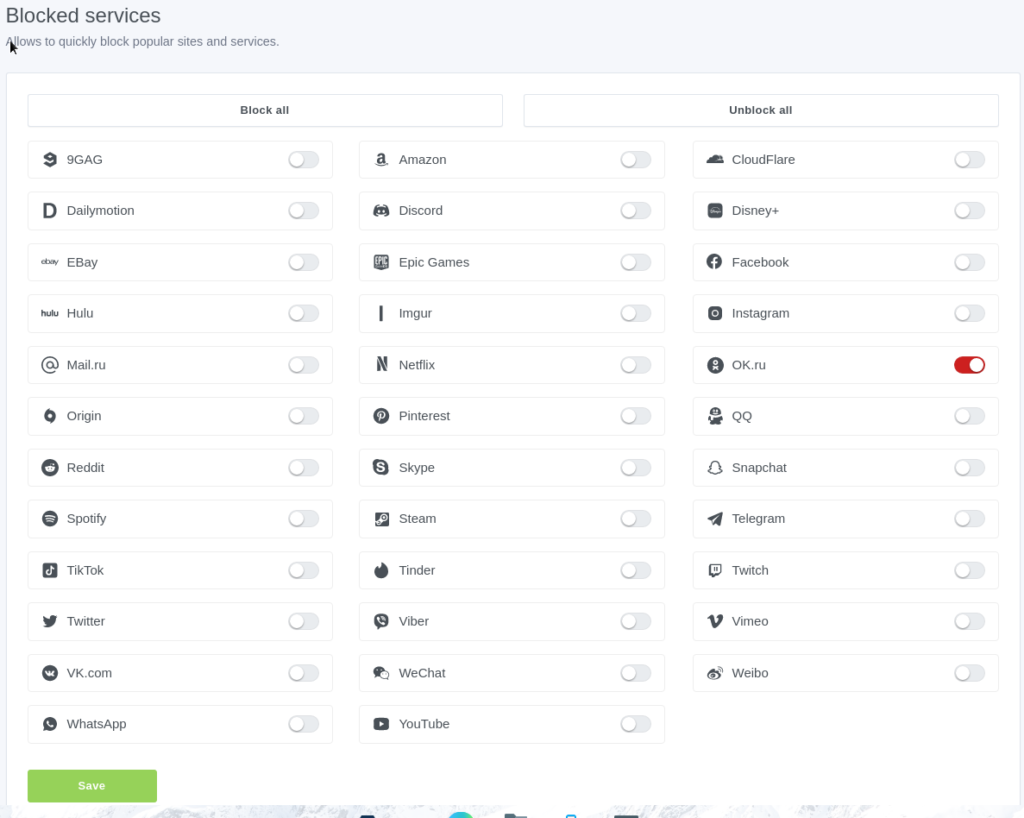
Overall the Dashboard for AdGuard home is a huge improvement over Pi-Hole both visually and functionally.
Features
Feature wise AdGuard Home has a lot going on. So I’ll just list them out here;
- Force Safe Search
- Load Balancing or Parallel request routing of DNS
- DoH, Dot, and DNS over Quic support.
- Customizable Cache size (store the answer for more domains which speeds up requests)
- ACLs
- HTTPS support (kinda. You have to get the cert yourself but you can paste the contents into the web browser to upload it).
- Individual Client settings including custom block lists and upstream DNS servers
- One click add blocklists
- Blocked Services
There’s a lot to like when it comes to AdGuard but there are also some problems with it.
Problems with AdGuard Home DNS
Adguard fixed a lot of the complaints I had with Pi-Hole but in the process introduced a few of its own, namely it’s future.
Is AdGuard Home Going to be replaced?
AdGuard the company has spoken publicly about their desire to make a cloud hosted DNS based adblocker like AdGuard Home but without having the end user manage the infrastructure. Now, I don’t think AdGuard is going to completely kill AdGuard home when they roll out their public cloud version but stranger things have happened.
Limited Long Term Storage
AdGuard has an upper limit storage of 90 days before logs start rolling off. Now I’ll admit 3 months is a long time but I’m the type of person who likes to keep logs for years so I can do analysis against them.
Bad Group Management
While AdGuard does support per-client requests similar to Pi-Hole in my opinion Pi-Hole does it much better. Lets say I have 5 computers that I want to allow 1 domain for. With adguard I would have to manually add all 5 of those computers and the manually add that 1 domain for all 5 of them (10 actions total). Expand that by say 10 domains for 5 computers (55 actions total).
With Pi-Hole I would make a group, add the 10 domains to the group and then add the 5 clients to the group for a total of 16 actions. Pi-Hole handles groups drastically better than AdGuard.
pfBlockerNG
The final one I want to talk about today is pfBlockerNG. This tool is also free and opensource however it currently only works in pfSense which immediately puts it out of reach of a lot of people. pfBlockerNG is built directly into the router itself which eliminates the need to run extra hardware for adblocking. Being built directly into the router gives pfBlocker a lot of advantages but also a major disadvantage, but before we get to that lets talk about the beast that is this things dashboard.
The Dashboard
The dashboard for pfBlockerNG is all over the place with varying degrees of usability. On the home screen of pfSense you have a quick look stats similar to the others.
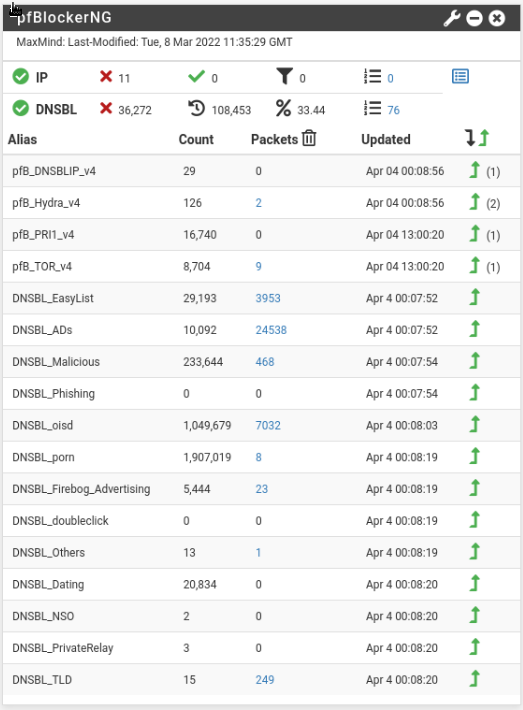
You can see how many queries were on your network, how many were blocked, what percentage was blocked, and then you can drill down into which blocklists specifically are blocking traffic. The numbers are clickable and bring you to a log page where you can see the specific domains:
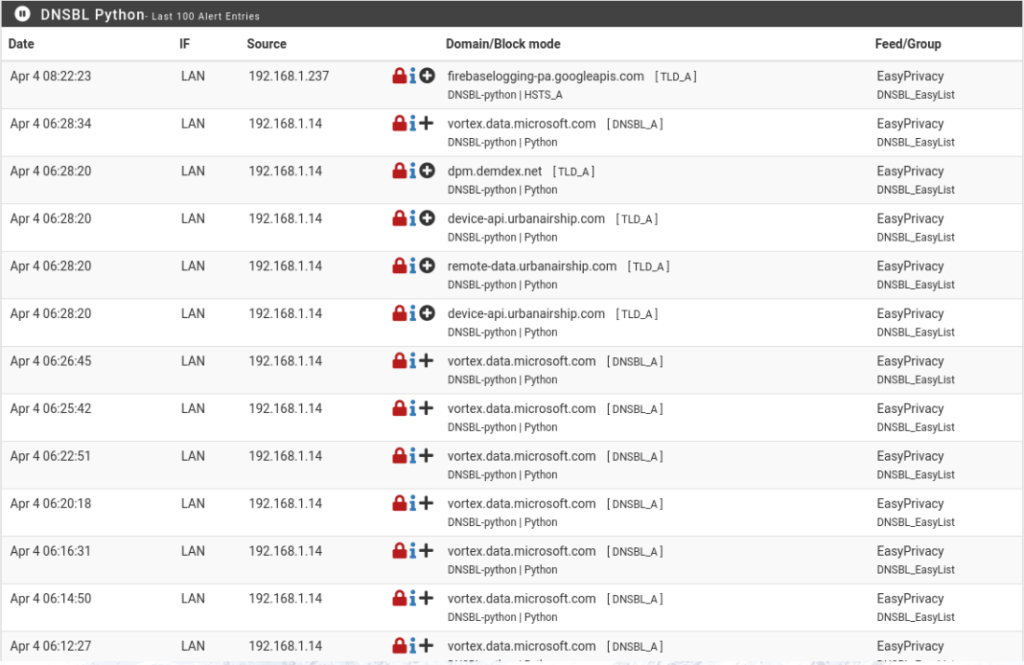
Ok. So far so good. Managing this thing however is a beast. You have 8 main options with multiple sub option under each main option.
Inside of one category you have multiple options with various different symbols
and sub categories, some of which are collapsed while others aren’t
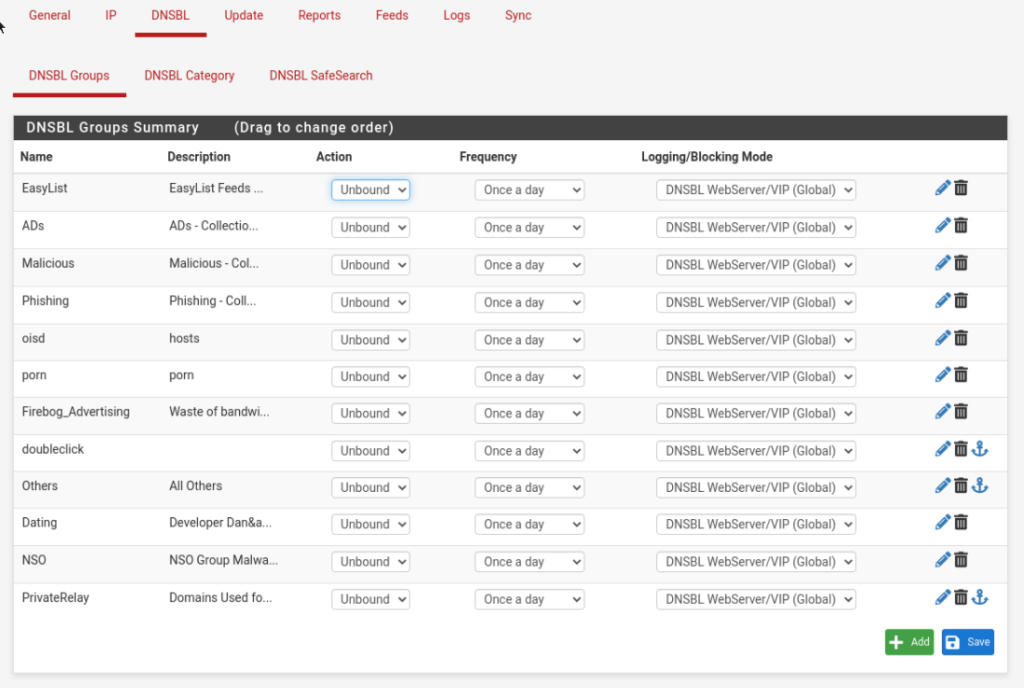
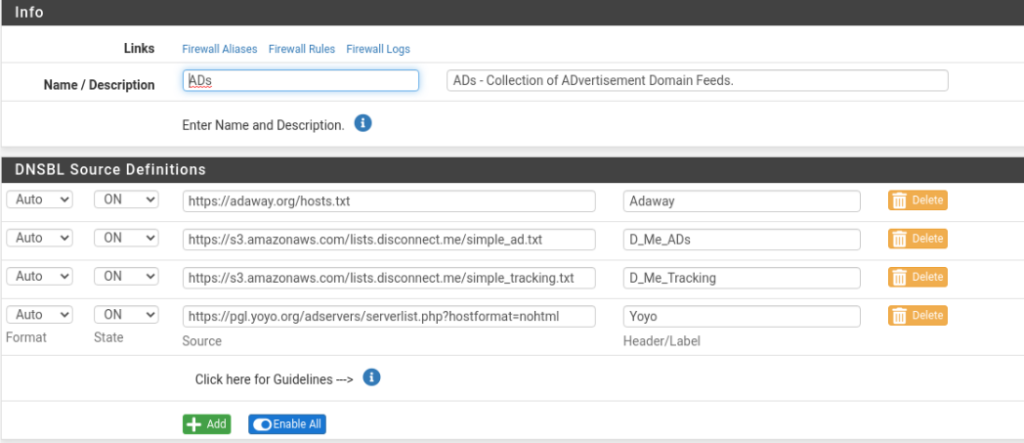
4 separate domain feeds. Managing through all of that and eventually the pfBlockerNG will start working and you can review logs. The Reports category has 8 sub categories under it
Which give you traditional logs
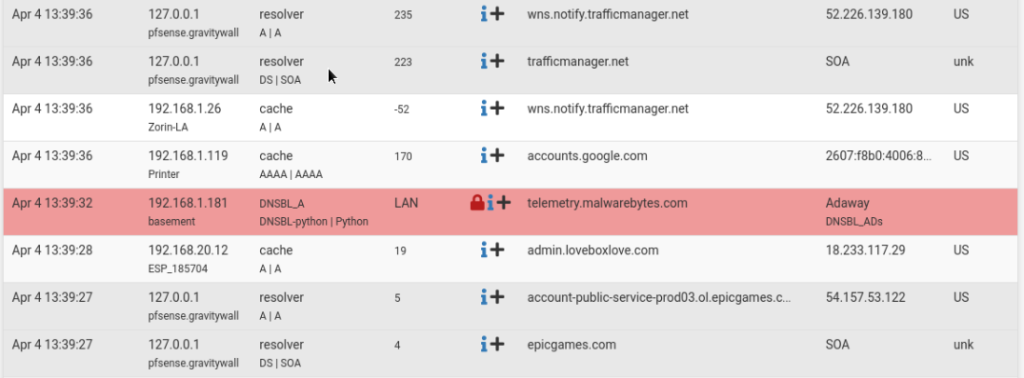
As well as graphics and charts.
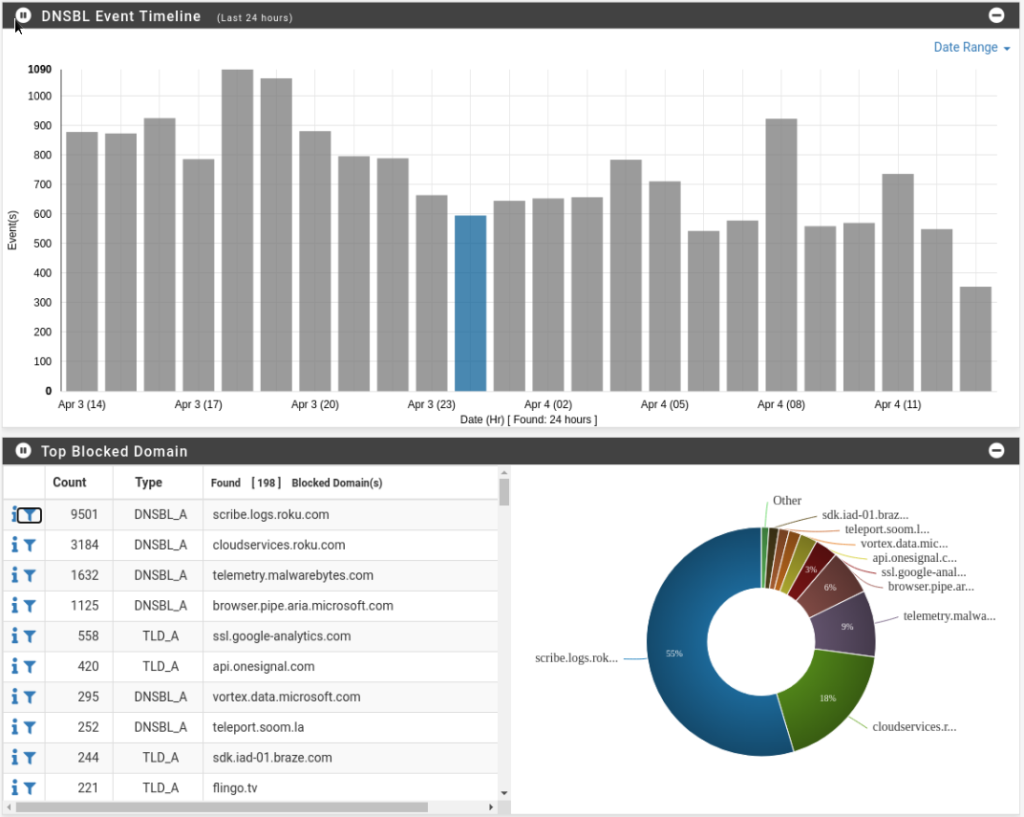
I bring all of this up, with lots of pictures, to say that I really dislike the dashboard of pfBlockerNG. In fact I dislike the dashboard so much that I set up an ELK server to store all my logs for me and give them in a manner which I can actually use.
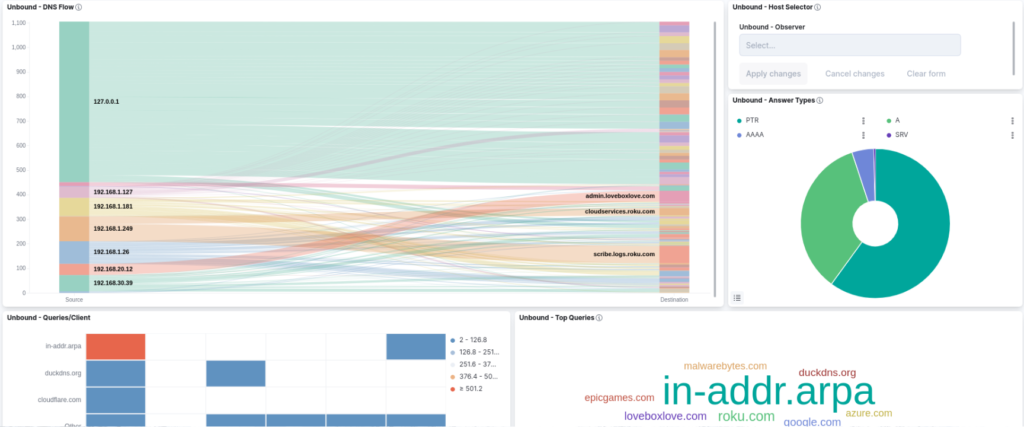
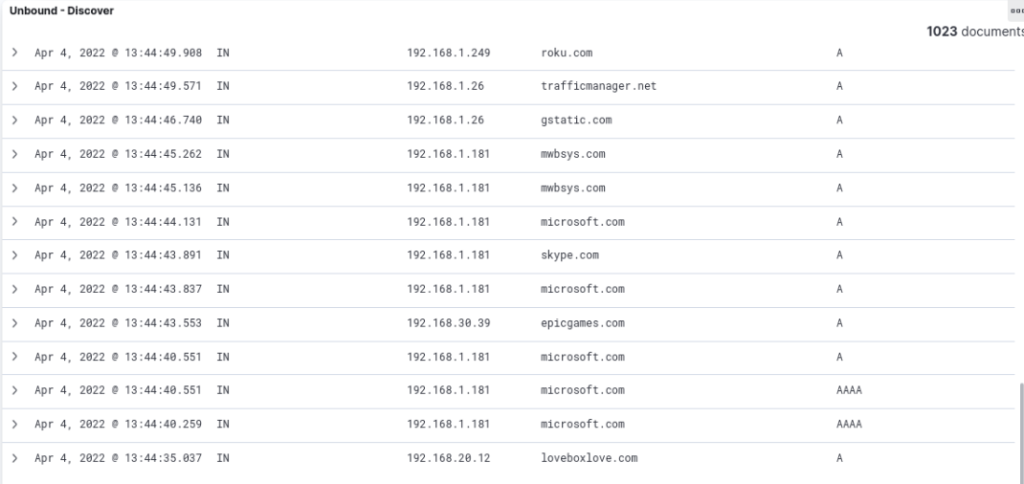
Despite my headaches with the pfBlockerNG dashboard I still wouldn’t trade it because of the benefits.
Features
Since pfBlockerNG is built into the router it has a lot of features that I like.
- IP block lists and DNS block lists
- pfBlockerNG benefits from being directly integrated with the Firewall. This means that pfBlockerNG can automatically update the firewall with block lists for known bad IPs.
- VLAN support
- Unlike with Pi-Hole and AdGuard, pfBlockerNG supports VLANs automatically. Pi-Hole and AdGuard support VLANs technically but you have to tell them to listen on other interfaces and set up deliberate routing to get the packets there.
- Forced Safe Search
- Syncing between devices
- DoT support
- A block page
- This one is a personal preference but I like knowing when my DNS blocker blocked a domain.
Problems with pfBlockerNG
As much as I like pfBlockerNG there are some problems, and they’re big ones. I’ve already talked a lot about the dashboard but its honestly terrible. I can’t actually explain how much I dislike the dashboard. It’s just bad, but the other problem is worse.
The internet breaks on a pfBlockerNG update. Whenever pfBlockerNG gets updated it causes Unbound to become out of sync with the DNSBL and therefore it won’t resolve any domains for several minutes while I force a resync.
Finally pfBlockerNG is too complicated to get started initially. I’m a fairly technical person but I still had to review blog posts and guides on how to set this up.
So which one would I recommend?
At the end of this I think the answer is simple. If you have a pfSense then I’d highly recommend pfBlockerNG, but if you don’t have a pfSense then I’d recommend AdGuard Home. This was a difficult decision for me. I had a lot of nostalgia for Pi-Hole after working with it for years and it helping me get into Network building; however, Pi-Hole seems very much like a project of a bygone era. It does it’s job well but that’s all it does. It has too many security concerns, it doesn’t support things like DoH or DoT natively, the dashboard desperately needs a facelift, and outside of it’s excellent implementation of groups it doesn’t do anything not already done better by someone else.

