
The short answer is yes. Yes, your Chromebook can in fact get a virus, just not in a traditional sense.
As a computer security specialist, I get asked a lot “Why don’t you just use Mac (or Linux)? They don’t get Viruses.” I usually chalk this up to ignorance and deliberate marketing. Apple toted the concept that Macs don’t get viruses when they knew full well that they can. The only reason they didn’t was because there wasn’t enough of them to make the effort worth it. That’s still largely true today for Macs, and I shouldn’t have been surprised to learn that ignorance and deliberate marketing have made people start to think the same thing about Chromebooks.
Google has really stepped up their marketing of Chromebooks recently and included in that marketing campaign is a campaign that Chromebooks have “Built in Anti-Virus”, and while this is technically true. It’s different from being “Virus Free”.
Chromebooks have taken on an almost Mac-like persona of being “unhackable”, except. It wasn’t true for Mac and it’s not true for Chromebook either. It’s not uncommon to see people claim that Chromebooks have never been hacked and can never be hacked.
So is this true? No.
Looking at the Vulnerabilities
Since 2010 ChromeOS has had 45 CVEs recorded for it. When you take an average of all the CVEs you get a 9.1/10. 45 CVEs in 11 years isn’t very many granted but when they’re found they’re usually big. 20 of the 45 CVEs were over 9.0 and 14 of those were a 10/10.
That means that roughly 1/4th of all the vulnerabilities in ChromeOS were remotely accessible, easily scriptable, didn’t require authentication, and granted complete control over the system. That’s a lot.
It is worth noting that the last CVE recorded for ChromeOS was in 2019 and it’s common for ChromeOS to go 2-3 years without a vulnerability discovered. However, even without a vulnerability ChromeOS is not completely secure.
Bad things come in Threes
While ChromeOS does make a lot of good security decisions (like no admin account) it also makes some bad security decisions in the name of greater flexibility for the end user. When ChromeOS first came out 11 years ago it was extremely limited in what it could do. The original ChromeOS was a web browser and that’s about it; today’s chromebooks however are web browsers, locked down Gentoo Linux systems, android emulators, and Linux emulators. All of these additions to the system introduce new attack vectors for an adversary.
Android Malware is ChromeOS Malware
Today’s Chromebooks run the Android apps through the Google Play store in an emulated environment on the system. This means that any Malware that runs on Android can also run on your Chromebook. MITRE refers to this technique as “Deliver Malicious App via Authorized App Store” [T1475]
Android Malware comes in three forms. You have malware that abuses permissions to collect data and sell it, malware that engages in click fraud where it clicks on ads in the background to make money, and finally you have truly malicious apps that outright try to steal sensitive information like banking credentials from the user’s phone.
All three types of these apps are available in the Google play store, some of them even have up to 1 billion installs.
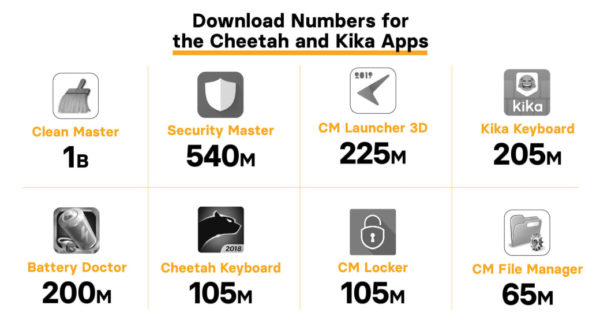
These malware apps are just as prevalent on Chromebooks as they are on Android Phones because they’re using the same store. Even legitimate apps can turn malicious as developers sell apps, dev accounts get hacked, and malicious code is pushed into legitimate apps.
Linux Malware is ChromeOS Malware
While it’s true that ChromeOS is not straight Linux. Google has taken a lot of care to make the underlying ChromeOS a secure environment to work in, but the Linux VM built into the system doesn’t get the same love. Despite what people love to claim about Linux being unhackable there are still tons of techniques which work against Linux. You can find them, and their sub techniques, here on the MITRE ATT&CK matrix.
In recent years, around 2017/2018, Google added a Linux environment that users can enable in the settings of the Chromebook. This is a full-fledged Linux environment running in a virtual machine on Chromebook. The Linux VM allows power users to install more advanced software than they might find in the Google Play Store. On my Chromebook I use the Linux VM for installing RDP apps like Remmina to give me greater control over RDP and using advanced tools like grep when working with large abstract datasets. I honestly couldn’t imagine using my Chromebook without the Linux VM installed, and I know there’s a large section of users over on r/chromeOS who feel the same.
Users who choose to enable the Linux VM on their Chromebook are increasing their attack surface. One of the most common attacks against Linux is users running unverified scripts or unknown commands. Users who aren’t familiar with Linux will find commands and scripts online on sites like Stack Overflow and execute them blindly.
I shouldn’t have to tell anyone that blindly running commands and scripts on your computer is a bad idea, and yet people still do it anyways which leads to malware running on their Linux environment.
Browser Malware is ChromeOS malware
The last attack vector I want to discuss is browser base malware, more specifically browser extensions [T1176].
One of the greatest things about modern web browsers is the ability to completely customize your user experience using extensions. There are some extensions which are necessities like uBlock Origin and HTTPS Everywhere. There are other extensions which are nice to have like Enhancer for Youtube, and then there are bad extensions and malware in the Chrome Store.
Extensions are a tricky thing to deal with. Most users don’t know what accesses their extensions have; what they can see, what they can change, etc. Under the current extension manifest (manifest v2) extensions can intercept and manipulate network traffic coming from the browser. This is how your adblock extension works. It monitors the network traffic looking for connections to known ad hosts and then blocks those connections before they finish. While adblock uses this technique to make the internet a better place but malware also uses this technique to intercept your network traffic and steal passwords.
Google is working on fixing this with their Chromium manifest v3 by preventing browser extensions from intercepting network traffic (and preventing adblockers from working at the same time), however until manifest v3 is officially rolled out (it keeps getting delayed amongst pushbacks from adblocker advocated, me included). This means though that browser extensions are still able to intercept network traffic.
In December 2020 security company Avast released a report of their discovery of 28 Chrome extensions containing malware with a combined download total of over three million. According to Avast the browser extension malware had the ability to steal user data including personally identifiable information such as birthdates, addresses, and passwords.
Unlike traditional malware most Antivirus solutions don’t look at extensions installed in the browser and with features like browser sync a user could easily transfer this malware between computers as they sign into their Chrome on a new system. Since this malware exists in the browser it’s also platform agnostic. The Chrome you install on Windows is largely the same Chrome you install on Mac. The extensions are built for the Chrome webkit so they work regardless of if you’re using Chrome on Windows, Mac, Linux, or ChromeOS. This means that malicious browser extensions will still work on ChromeOS the exact same as they would on your Windows 10 computer.
But there’s no root (admin) so it doesn’t really matter…right?
Wrong.
There’s this misconception in the world of cyber security that the end goal is always to get root/admin on the system. A lot of this spawns from the numerous capture the flag challenges out there where getting root is usually a requirement before you’re able to find the flag. In the real-world things aren’t always so cut and dry, getting root isn’t always the end goal.
There are lots of malware in the world that don’t require root privileges to run. Several months ago, I wrote a post on my findings researching a Monero mining botnet. Nothing I discovered in that post required admin permissions to run, but the result was still the same. There was malware on the system, making the system sluggish by using up resources to mine Monero coin for someone else.
Malware isn’t always trying to get admin, getting admin will almost help the malware achieve its objectives, but it isn’t required. Browser extension malware can still steal your bank password without needing admin access on the machine. Crypto Coin mining malware doesn’t need admin to use your resources.
I mention this because while Google made a good decision by removing the admin account from Chromebooks it doesn’t mean the malware you can get on Chromebooks is invalid. Your Chromebooks can, and do, get malware.
Stay safe.

