The real truth from someone who isn’t trying to sell you a VPN: Also a reason why you should avoid Nord.
For those of you who have read some of my other thought pieces you’d know that I don’t have a very high opinion of commercial VPNs. While I still use one for research purposes I think that most VPN companies have started trying to capitalize on fear, uncertainty, and doubt (FUD) to try and sell their product. I still believe that and I want to take some time to dispell that FUD from one of the largest VPN providers, Nord VPN.
What can someone do with my IP address? | NordVPN
archived 11 Jun 2021 14:23:51 UTC
Nord VPN is perhaps one of the most popular VPN providers around, largely in part due to their aggressive marketing tactics on Youtube. Nord has gotten quite the name for itself as a fast, secure, and safe way to protect your IP, stop, hacker, and keep yourself safe online. Only one of those is true. I wasn’t surprised to see the above article and was actually hopeful that they would dispel some myths about what an IP is. To their credit a lot of what they say here is accurate, but it’s definitely spun in a way to create FUD and sell you a VPN. Even the top of the page where it lists my IP and says I’m “Unprotected” in red lettering is designed to create fear.
So let me tell you what someone can actually do with your IP address, from someone who’s not trying to sell you anything (I don’t even run ads on this site).
What is an IP address?
Your IP address is a series of 1-3 numbers repeated four times between 0.0.0.0 and 255.255.255.255. These numbers aren’t arbitrary, they link back to binary where 0.0.0.0 is 00000000.00000000.00000000.00000000 and 255.255.255.255 is 11111111.11111111.11111111.11111111. We’re not going to get into a discussion of breaking an IP address into its binary number, the point behind this section is to show you that there are very finite parameters for an IP address. Someone could start writing down numbers and eventually they will hit your IP. But let’s talk through what this actually means.
The Home Address analogy:
Your IP address is a number provided to you by your Internet Service Provider the same way an address is provided to you by the post office. Because of that similarity we use the address as a reference when we talk about IP addresses; however, this is a bit of a flawed analogy.
With a postal home address that number is linked directly to you, but that’s not the way the internet works, a better analogy for this is a P.O. box. With a P.O. box I can give you the address of the box and you won’t have my actual home address. My actual address is known only by the Post Office itself.
Your internet service is largely the same way, with one major difference. Someone sending mail to a P.O. Box must include a name of the recipient. If the name doesn’t match then the Post Office is supposed to reject the mail. This means that someone has to have at least your name. With your IP address your name and address are both kept private by the ISP.
How can people get my IP address?
Simply put; literally anything you do on the Internet is providing your IP address. By reading this you are providing me your IP address (I don’t actually log them, but you are providing it). There’s a very simple reason for this; much like the Post Office, in order for me to actually answer you I have to know how to reach you. See what happens is when you clicked whatever link brought you here your computer made a request for this webpage. That request is called a GET request. Websites get thousands to millions of these GET requests every hour and have to differentiate who gets what reply. That’s where your IP gets involved.
Anything you do on the internet provides someone your IP, that unfortunately includes the unsavory folks.
What can someone learn about me with my IP?
Simply put; not much.
Think back to that P.O. box example. If I provided you my P.O. box information but without my name what would you learn? You’d learn what city I lived in, and if the city was large enough you could guess what part of the city I live in as I probably will be going to the closest Post Office. But as mentioned previously you wouldn’t have my actual address because only the Post Office has it, so you would need to get that information from them somehow.
Let’s look at what Nord says

Nord is correct, but again beware of the FUD. I mentioned it earlier that your IP does not include any actually identifying information about you, such as your name, which should be considered at least the minimum required to find someone. In Nord’s example lets look at the information a cyber criminal would need.
- They would need to be able to see your social media.
- They would need at least your name to look you up in a phone book.
This certainly isn’t as simple as Nord makes it seem.
What can someone do with my IP?
DDOS
Again, the answer is not much. For the average home user, the most they could do is something called a Denial of Service (DoS), or a Distributed Denial of Service (DDoS). I’m not going to explain the differences here as they both have the same end goal. A DoS can result in you not being able to access the internet because your home router is getting flooded with traffic you didn’t ask for.
This sounds annoying, and it certainly is, but that’s about all it is. Most DoS attacks against a home user only last a few minutes and they’re usually very easy to stop. A DDoS however is not actually a hack. The attackers do not gain any access to your network, or private information.
What does Nord say?
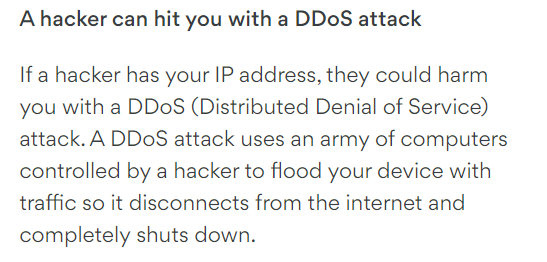
I actually don’t have much to say here other than in order for a DDoS to completely shut down a device they would have to completely overwhelm it. Otherwise, Nord is using FUD language by saying things like “an army of computers” but otherwise its fine.
Can they hack me?
This answer is complicated as hacking has a multitude factors which need to be considered. For the average home user, the answer is probably no. Unlike in movies hacking is not as simple as hitting a few keys and bam you’re in. Hacking requires 3 main things, a vulnerability, an exploit, and a payload (you can read more about those here). Router level vulnerabilities are uncommon because your device has something called a Firewall which blocks outsiders from being able to connect.
For most people reading this you’re probably not at any danger of being hacked….Unlike what Nord says.
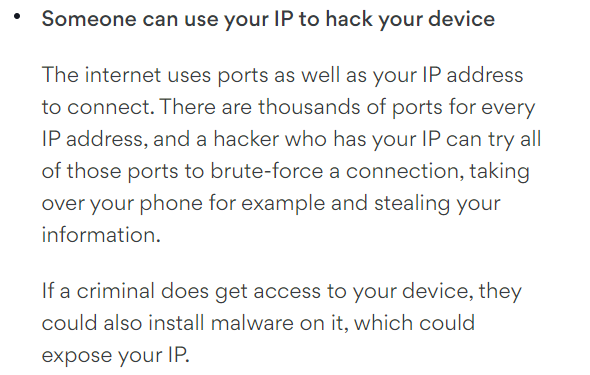
Open Ports:
I guess I have to talk about this because Nord isn’t going to. Ok here goes. Remember that Post Office analogy we’ve been referencing? We’re going to be using that again, except this time we’re not delivering to a P.O. box, we’re delivering to an Apartment Complex. Your computer is an apartment complex and I want to send a letter to a specific person who’s expecting it. I can’t send that letter straight to the complex or the person will never get it, so I need to send it to a specific apartment number.
Ports work similarly. Every device on your network has 65535 ports on it. Everyone one of those ports could be a completely different service listening for something, or you might have one service using several ports, or you may be using no ports at all (not likely). Some ports are always going to be in use depending on the type of computer. For example Windows computers will almost always use ports 135, 139, and 445. Linux computers will generally use port 22.
Regardless of what type of device you’re using there is one thing that is a universal truth. Something must be expecting a connection. You can bring a letter to any random apartment inside the complex but if there’s no one there expecting the letter it won’t matter. Computers are no different. “Brute-forcing” a connection is perhaps the largest FUD in this entire article and it’s the reason I wanted to write this.
Remember like four paragraphs ago when I mentioned a Firewall? Well, your router has one of those, and its whole job is to prevent people from making a connection you don’t approve of. Think about the lock on your front door. When it’s locked people can’t just walk right into your house. You must first unlock the door to allow them to come in. The same is true with a Firewall. If you don’t unlock the lock (called port forwarding) then nothing is getting through. A hacker can “brute force” your ports, and believe me thousands of bots are attempting this tens of thousands of times a day already, but it won’t matter because the firewall will stop them.
Let’s also take a second and talk about “taking over your phone”. This statement is so ludicrous that I’m actually surprised Nord put it in this article. Taking over a phone is a monumental feat. Android and Apple devices are actually incredibly secure. 99/100 times phones are compromised by getting a user to install a malicious app. Androids are worse about this because they allow apps from untrusted sources (installing an .apk file from the internet), but Apple devices also have malware in the Appstore. Actually, hacking a modern smart phone is damn near impossible. In fact, it’s so difficult that Google is offering $1M for anyone that can actually pull it off.
I’m beyond pissed off about this, but it’s actually not the worst thing in this article. That will come later.
I’m not going to dispel the rest of these in detail, they’re all FUD. I am going to draw attention this one in particular.
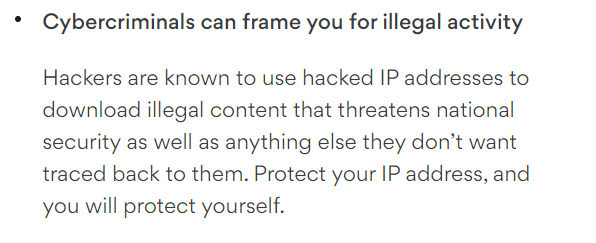
“National Security” concerns
What a slippery slope
Oh man. This one is really something, again its actually not the worst thing on this blog surprisingly. A hacker with your IP address is going to download something that threatens national security. Oh man. There’s so much wrong with this one but I’ll just point out this instead.
“A slippery slope argument, in logic, critical thinking, political rhetoric, and caselaw, is an argument in which a party asserts that a relatively small first step leads to a chain of related events culminating in some significant effect. The core of the slippery slope argument is that a specific decision under debate is likely to result in unintended consequences. The strength of such an argument depends on whether the small step really is likely to lead to the effect. This is quantified in terms of what is known as the warrant. This type of argument is sometimes used as a form of fearmongering in which the probable consequences of a given action are exaggerated in an attempt to scare the audience, although, differentiation is necessary, since, in other cases, it might be demonstrable that the small step will likely lead to an effect.” – Wikipedia
That’s right folks, if you’re not using Nord VPN then a hacker is going to steal your IP, and if a Hacker steals your IP they’ll download illegal material, and if they download illegal material they might download Nation Security information, and if they do that you might go to jail!
That’s not how this works. That’s not how any of this works. For one thing Forensics exists, which will be used to determine if it was actually you downloading anything. And second remember how I said your IP was like you’re P.O. box address? A criminal could have their drugs sent to your P.O. box but if they don’t have a key to the box they can’t open it to get their drugs. Well, guess what. If the hacker doesn’t have access to your network then they can get any illegal material they sent to your IP. Also remember how we said a Firewall keeps people out unless you let them in? Yea. That again. If a Hacker is not on your network and merely uses your IP then your Firewall will reject it because you didn’t tell the firewall to accept it. What Nord is trying to say here is that with your IP a hacker MIGHT be able to hack you, and if they are able to they MIGHT be able to download illegal content.
Ok, so…I have seen cases where a neighbor hacked into their neighbors Wi-Fi and used that to stage illegal content so it wouldn’t be tracked back to them. These cases happen because Wi-Fi is significantly less secure than a Firewall. The big difference here is location. In order to actually hack the Wi-Fi they have to be close enough to pick up the Wi-Fi signal, (i.e. not miles to thousands of miles away).
Nord’s biggest offense
Scamming a Scam Victim:
I’ve alluded to this several times so let’s get to it. Nord attempted to use FUD to scam the victim of a Tech Support scam into buying Nord.
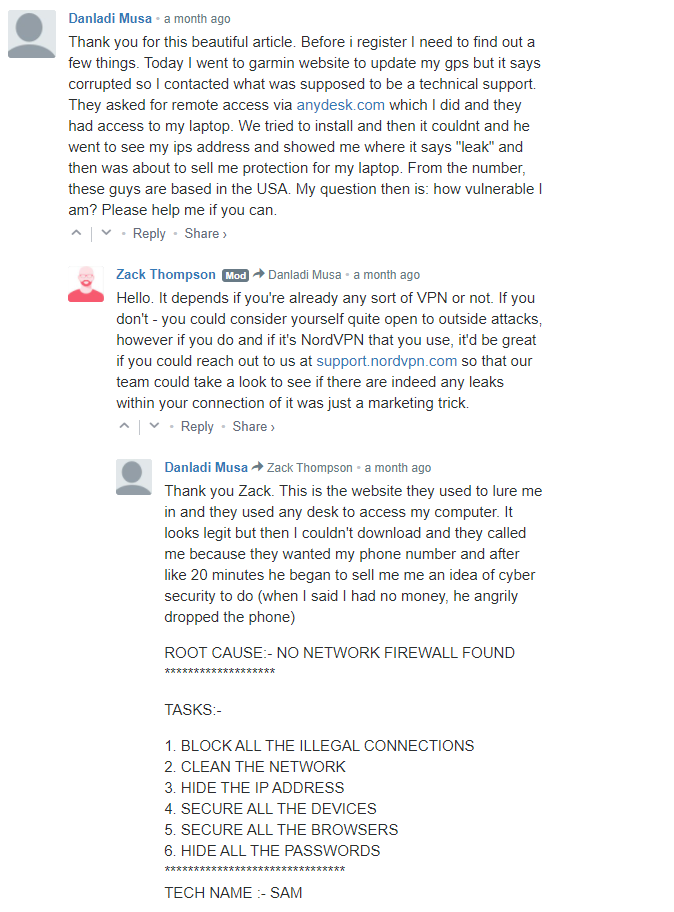
I wish I was making this up but I’m not. It’s in the archive for you to see if you want. The victim (Danladi) went to a website and got a scam popup. The victim called the scammers and talked with them. The Victim allows the scammer access to their computer and the scammer says something about “leaks” (completely fake). The NordVPN mod (who is different than who wrote the article) then used FUD to try and convince this victim to buy Nord.
“If you’re not using a VPN you could consider yourself quite open to outside attacks.”
NO NO NO NO! BAD NORD! BAD! A VPN does not protect you from outside attacks. You know what does? A firewall and proper user education. A VPN would have done absolutely NOTHING to stop a scammer from gaining access to this user’s computer. The scammer, just like Nord, used fear to get the user to call and download a remote access tool (anydesk).
Nord is using fear of this scammer to try and get the user to download a VPN. This is just shameful activity by a supposedly professional company.
Conclusiong
And a TLDR:
What can someone do with your IP?
Pretty much nothing.
Do I need to be worried that someone said they have my IP?
No.
If I’m getting DoS’d what can I do?
Unplug your router for about 10 minutes. Most ISPs will assign you a new IP. If your IP doesn’t change after 10 minutes call your ISP and ask them what the DHCP lease is set to then unplug your router for that time.
Do I need a VPN?
Should I get one?
You can, but I wouldn’t recommend one from Nord.
Is Nord VPN good?
I wouldn’t use Nord VPN is they paid me.

