Introduction
If you’ve spent any time in the world of cyber security, you’ll know that one of the things expected is continuous learning. As a security professional you are expected to live and breathe this stuff. I’ve found that some of my greatest learning moments come from when I am building and working on my network. I’d learn about something at work and decide to come home and see if I can replicate it there. Thankfully my wife had the patience of a Saint as I broke the network multiple times. I thought it might be fun to look back at my network over time

Network 1:
Back when I first moved out on my own (before I started my career in Cyber Security) I didn’t really have an understanding of networking or Cyber. I thought I understood computers pretty well, but boy was I wrong. Unfortunately, at this time I didn’t bother making a network map so this map is based off my memory from years and years ago.
My network back in those days was very simple, I didn’t have very many devices back then. What I had was two routers connected together in a Double NAT (although I didn’t know that at the time). None of my devices needed to talk to each other so I never noticed what was happening in the background.
I first began to discover the problem when I needed to print from main PC and I couldn’t. I called Epson tech support to try and troubleshoot my issue. The tech support person had me run print a network test page from the printer and then run an ipconfig on my PC. He pointed out that the gateway was different. Although I didn’t understand subnetting I knew that each router created a different gateway. So, I knew that needed to move the printer to the other router.
That was the start of my researching on networks and cyber in general; something that would continue on through my career.
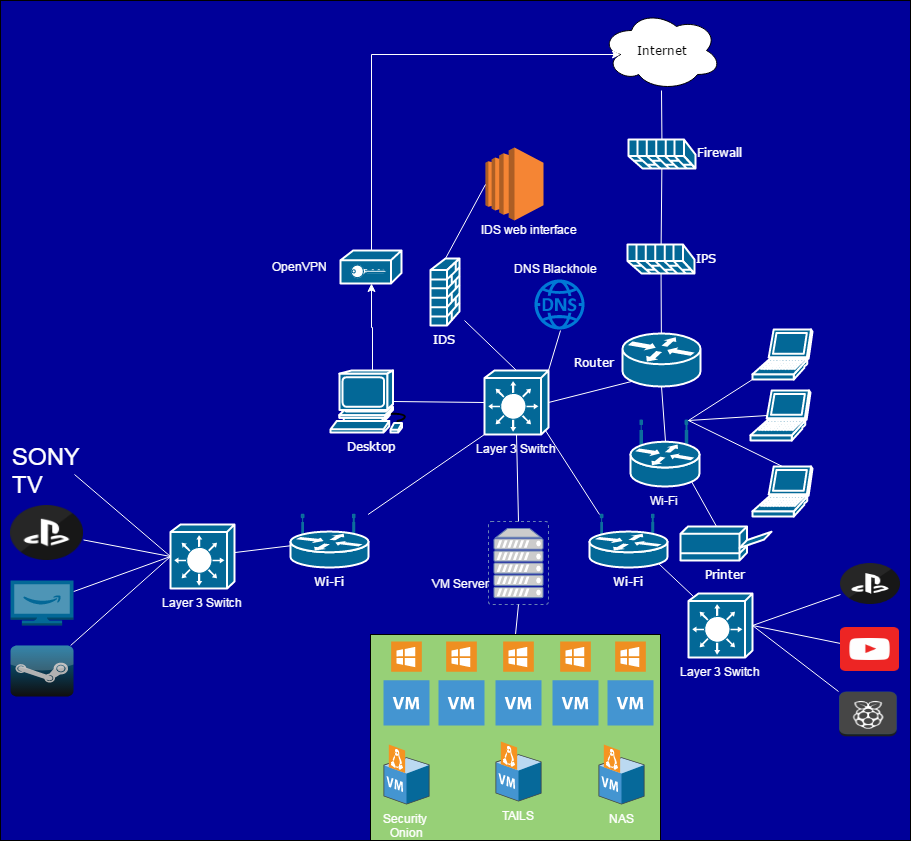
Network 2:
Sometime passed (around 8 months if I’m remembering correctly) and I found a mentor. I started my first job in Cyber security and delved heavily into learning networking. My mentor was a very senior analyst of 18 years. He taught classes to all the new analysts that covered the basics of networking. I soaked up his knowledge and began to rebuild my network. I also attended SANS SEC401 and got my GSEC cert.
Between these two things I started to work on my network. I had begun to learn about defense in depth. This is also around the time I learned about pihole (which will feature prominently in my networks from now on).
What I clearly didn’t know was how to make a decent diagram. This was made in Powerpoint and featured random colors that made no sense.
Network 2.b:
It’s pretty much the same as my original network 2 but this time I tried to add more colors to define things. At this point in my live I was learning about Mikrotik devices. spanning ports, and PXE booting. What I was trying to do with this network was to have the Microtik switch copy all network traffic over a span port to my IDS (running on a RPI3b+). I also had an old laptop that couldn’t run windows anymore. I wanted that laptop to PXE boot Linux (Mint Cinnamon) off a NAS.
My house still wasn’t as interconnected as it is now. At this point I was mainly focused with setting up security and getting every device I could off Wi-Fi and onto ethernet. There were unfortunately some things I couldn’t get working. While I got the PXE boot working it wasn’t working the way I wanted. I would eventually scrap it in my next iteration.
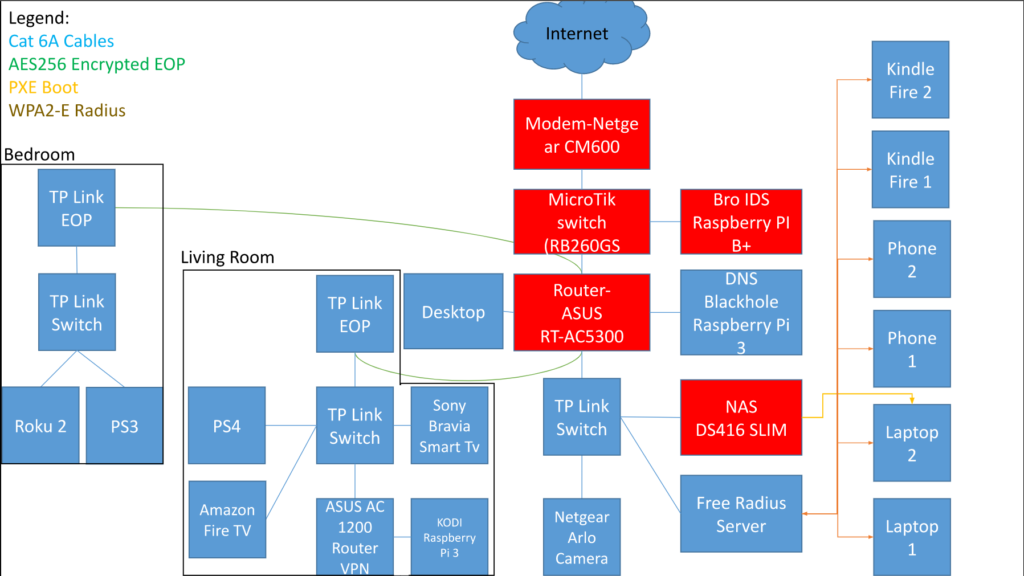
Network 3
Right off the bat you can see that I figured out to access a proper diagram editing software (draw.io, now known as app.diagrams.net); however, as I’m sure it’s painfully clear, just because you know how to access a diagram system doesn’t mean you can make it appealing. The dark blue background is awful, things are different sizes randomly, there’s odd colors for no reason, icons don’t make sense (what is that printer icon?); this whole thing was a mess.
I really hate this diagram but that’s why this historical look is so entertaining; it gives me a look back at how I’ve advanced overtime.
Where do I start with this one? I went less specific with this one but I added more technology. During this time I was going after my CCNA Cyber Operations.
I bought 3 Mikrotik hAP ACs and was learning how to configure them in CAPsMAN configuration. The 3 Wi-Fi nodes in this image are all those Mikrotiks. I really like Mikrotik routers, they’re a swiss army knife of networking, but good god are they difficult to learn. I finally found someone who makes really good instructional videos on Youtube. His name is TKSJa and he’s fantastic, highly recommend.
Another thing I started working on was my VM farm. I became involved with the CyberPatriot program as a technical mentor and started building VM training labs for them and the people I worked with.
This is also the point where I started really looking into VPNs, which I have some strong opinions on.
There are a few bad networking practices here that I’ll get into later.
I also wanted to make my training network more robust. I was starting to build ethical hacking labs and wanted to prevent anyone from accidently throwing exploits on the web. I marked a firewall there which lead to some confusion when I showed this diagram to people. They assumed my only firewall was there instead of another firewall on the edge router. Finally, with regards to the training network I decided that I wanted to ensure that any research on malware I did was isolated; so, accessing those machines required me to VPN into the training network and then RDP to the malware analysis machine. This allowed me to control an isolated malware analysis virtual machine with very little chance of a VM escape reaching me.
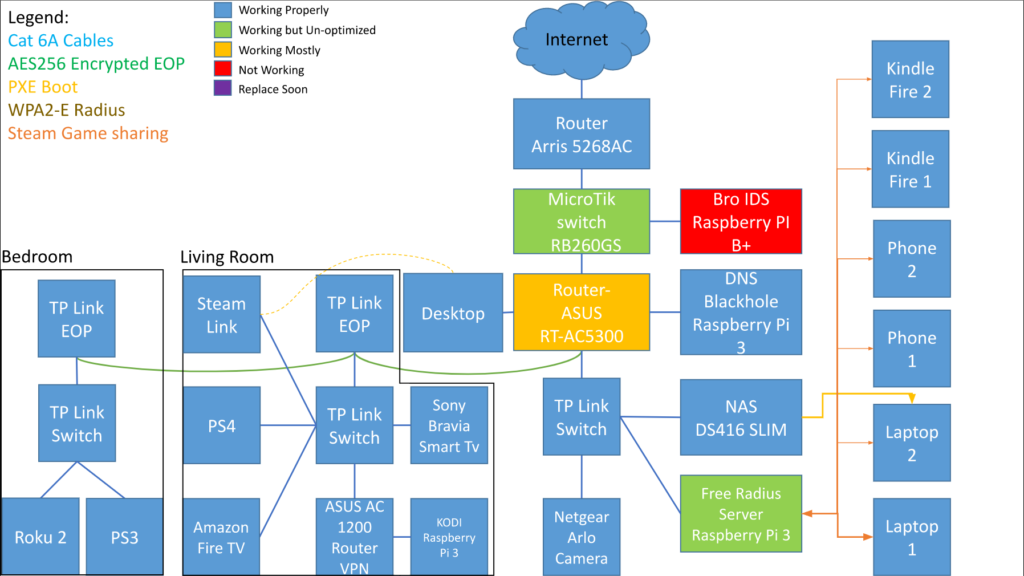
Network 4:
I grew tired of my old network and decided it was time for a major overhaul. This image is certainly quite significantly more pleasing to look at.
It’s mostly the same as the network above but in a more logical set up. I bought a Mikrotik RB3011 edge router which I used to divide my network into multiple subnets. My previous network was flat, everything (except the VM farm) was on one subnet. It wasn’t a great system. With the addition of the edge router (oh and I bought a server rack) I was able to divide the network into logical subnets to keep things isolated.
At this point I started getting more curious about studying network attacks so I set up a honeypot using a Raspberry Pi 3B+ and SANS’s Dsheild honeypot. I also used the knowledge about spanning ports to have my edge router to have all my network traffic sent to a Security Onion server for analysis.
I set up VPN concentrators in my network to allow remote access to resources, even though I forgot to include my NAS on this diagram.
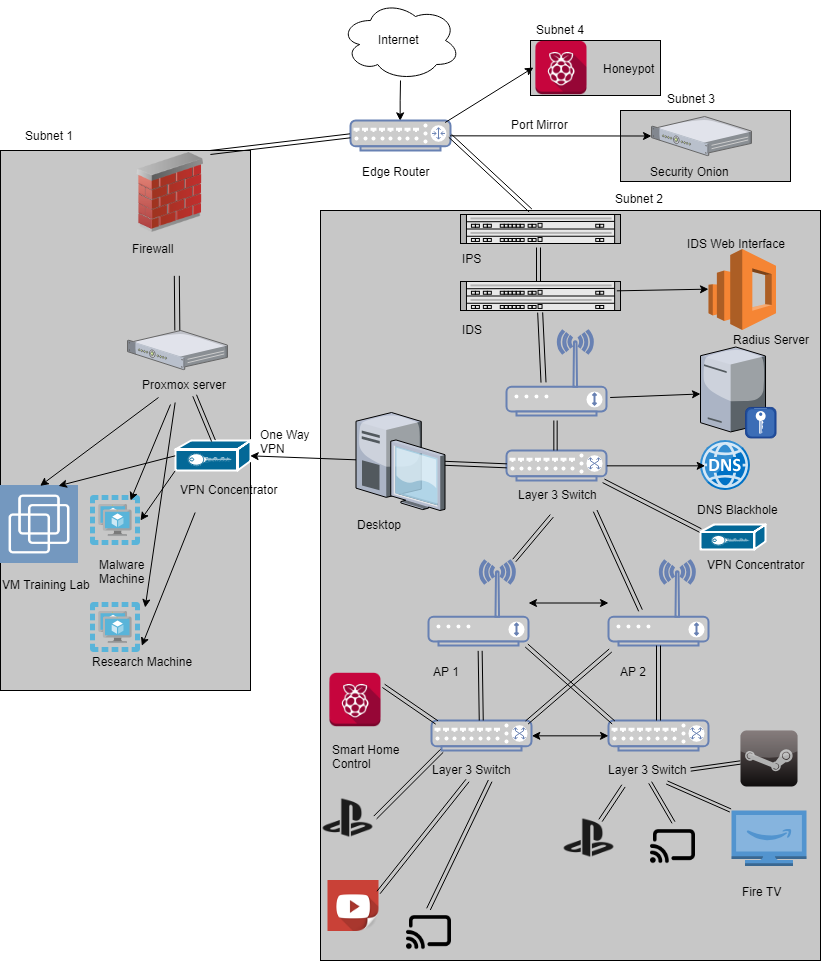
In the above diagram I had 3 hAP AC’s (which I still have) configured in CAPsMAN, unfortunately each of those were individual routers. They were all one subnet but different access points. At this point in my life my kids were young and losing the remotes all the time so I wanted a solution that was more minimalistic. I decided on Chromecasts (which I still love) and needed a better solution than 3 separate APs. The problem with different AP is that whenever I moved throughout the house my phone would disconnect and reconnect to the new AP. This would disconnect the cast and I would have to reconnect if I wanted to change shows (The show still worked, just control of the Chromecast dropped). To solve this, I set up my hAP ACs in a Mesh network. I still made the same mistake as previously by placing the APs before the switches. This is bad practice in general because it puts more work on the AP and means that if the AP goes down that leg of the network also goes down. I would fix this in the next iteration.

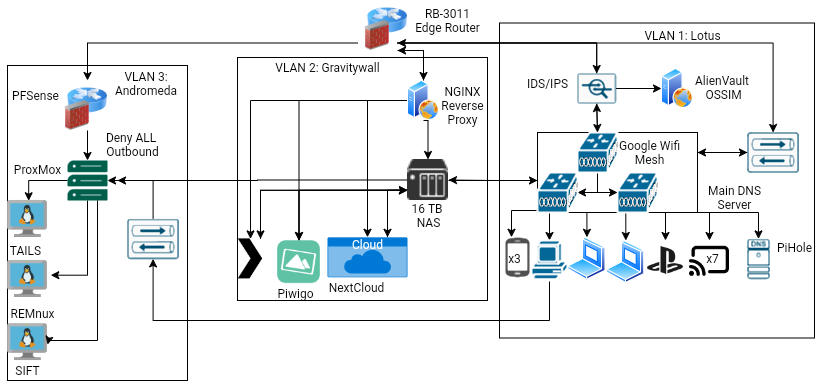
Network 5: Current:
This is my current network configuration. I took some time and re-reconfigured my network (again). When I started out writing this, I originally believed that this was my most drastic change, but I can see now that I was wrong. I think my most drastic change was between 3 and 4.
I made some minor changes to the network by replacing the Mikrotik hAP ACs with Google Mesh Wi-Fi. I still love the Mikrotiks but they weren’t playing well with Chromecasts and I just didn’t have the time to keep trying to configure them.
I also replaced Security Onion with AlienVault OSSIM. There was no real reason for this, I just wanted to experiment and I’m enjoying OSSIM so it’ll stay for now.
Perhaps the biggest change came at the unknown behest of my wife. After 4 years away my wife decided it was time to go back to college and finish her last year, but remotely. She had certain needs though. She needed a new laptop so she could work in peace from Starbucks after watching the kids all day; however, she had become accustomed to some luxuries I use at the house. Namely local folder redirection. All the folders on my computers are redirected to the NAS. This means that when you open the “Documents” folder on any computer in my house it pulls from the NAS instead of local storage. This system allows you to travel between computers in my house without losing documents. The problem as you might guess is that it only works locally. Pulling files via SMB remotely is a dangerous security practice. Now hold on before you start telling me about VPNs let me explain something. As much as I love my wife she’s not very good with technology. She’s put up with my antics for many years and sometimes those antics resulted in hours of internet outage while I fixed a network problem I caused. My laptops use a VPN bat script to connect automatically but she made it adamant that she didn’t want anything running on her school laptop; no scripts, no vpns, nothing that opens the command line. I now had to figure out a solution that gave her access to all her SMB files without SMB. Windows 10 Pro also wasn’t an option because I wasn’t shelling out another $100 for local file caching (although that would have been easier). One of these days I’ll do a blog post on all of the ridiculousness I went through to solve this requirement.
As I was working though this I discovered technodadlife on Youtube. A lot of his videos are on setting up Docker Containers for different things inside of an OpenMediaVault environment (which I was now using). It’s thanks to him that I began to learn how to employ docker containers in my network and oh boy did that go crazy. I started deploying docker containers just for fun, but to answers my wife’s requirement I deployed a Nextcloud docker, a NGINX reverse proxy, and used Letsencrypt to make the connection HTTPS. It wasn’t as seamless as local folder redirection but it worked, she had all of her files remotely and nothing was running on her laptop (this would later change at her request, but I’ll talk about that on the blog).
During the same time that I was building a solution for her I was also building my own domain, which in turn lead to this website you’re reading now.
Network of the Future:
I’ve had fun building this network to be as it is right now, and more importantly I’ve learned so much in the process; however, it’ll never be over. I will always have new goals for my network and I will continue to add to it as I learn more and more at work.
My new goals for my “network of the future” are:
- Security
- Simplicity
- Protection
Security is always my first and foremost concern. I want to make sure my network is protected as best as possible against malware. One of the things I’m looking to add in the future is Google Rapid Response. I’m working in Forensics right now and my thesis is on using forensics to enhance threat intelligence.
As I look back through my builds, I realize that security has always taken precedence and that sometimes has caused things to be overly complex. A prime example of this was DNS filtering using Pi-Hole. I use my Pi-Hole to block malware and ads but it had the unintended consequence of blocking websites my Wife needed for her school. She could still get to the website but she had to go to the site directly instead of clicking the link in Blackboard because Pi-hole was blocking redirectors. It added security but it also added an increased workload on her. Security, but not simplicity. I’ve written about this before and I still believe it to be true. You can’t expect end users to figure it out.
Even I’ve gotten confused with what resources are where on my own network and how to access them. I’ve built stuff and then forgotten that it existed. I want to simplify the network going forward. My goal for simplicity is that I want to be able to control 100% of the resources from my phone without having to change subnets but at the same time I want things to be isolated off without being able to connect to the network that has personal devices on it.
Finally, protection is starting to become a priority for me. I am differentiating protection from security based on goals. By protection what I mean is protection of my kids. When I started this project years and years ago my kids were babies, in fact I only had one kid. Now my kids are in school and have classes online. The internet is a bad place for kids so my network of the future will have a heavy focus on protecting them from the creeps online. I’ve started doing this with implementing Firefox policies and Google Chrome Policies.
Conclusion:
Building out and mapping my home network has been an enjoyable and educational experience. It’s given me a great understanding of some of the challenge that come with network engineering. When I first started years ago, I didn’t understand the importance of setting goals and priorities for my network. Now I’ve learned that you need to build with an end state in mind. I’m going to continue to build, improve, and learn with my network and can’t wait to see what lessons I discover with my Network of the Future.

